Every 39 seconds, a cyberattack occurs somewhere on the web
University of Maryland
What is Data Egress?
At its core, data egress refers to any data leaving a closed or private network and transferring to an external destination. This can happen in several ways, such as:
- Emails sent to clients or external recipients
- Cloud uploads to platforms like AWS, Azure, or Google Cloud
- File transfers via FTP, HTTP, or APIs
- Removable storage like USB drives and external hard drives
While data egress is an essential function of modern businesses, it becomes a problem when organizations lose control over where, how, and why their data is being transmitted.
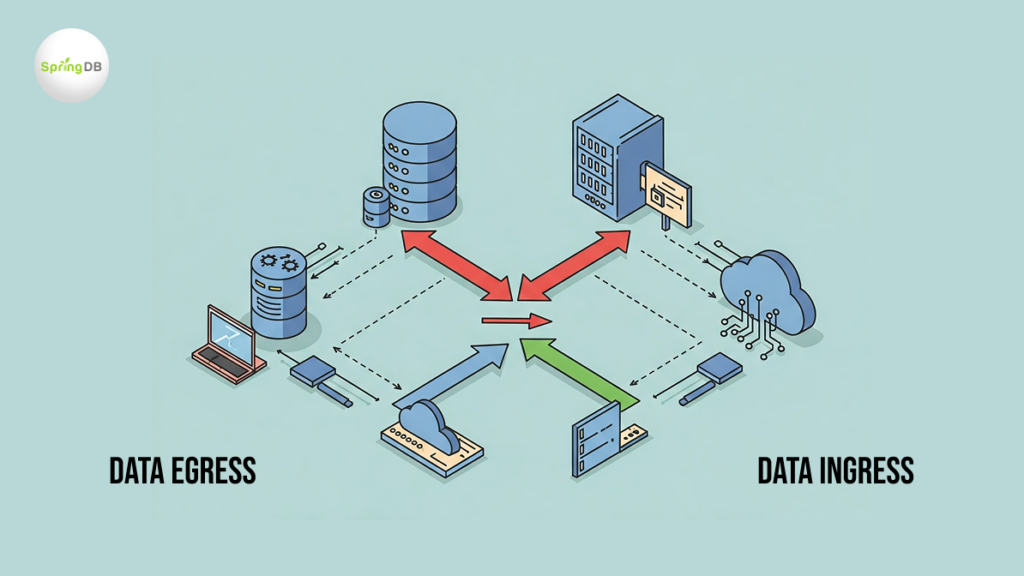
Data Egress vs. Data Ingress
It’s easy to confuse data egress with data ingress, but they serve opposite functions.
- Data ingress refers to inbound data—information entering a network from an external source.
- Ingress data can include software updates, inbound emails, or data imported from external databases.
- Egress data, on the other hand, is outbound—information leaving an organization’s network, often to a cloud provider, third party, or external recipient.
Why does this distinction matter? Organizations tend to focus more on ingress security, blocking unsolicited inbound traffic through firewalls. But many fail to monitor outbound data effectively—leaving them vulnerable to leaks, cyberattacks, and excessive cloud costs.
The Hidden Costs of Data Egress
Cloud providers don’t just charge for storing data—they charge when you move it out. And those fees add up fast!
Cloud Providers and Egress Fees
Most cloud platforms, including AWS, Azure, and Google Cloud, impose per-gigabyte fees on outbound data transfers:
- AWS: $0.09 per GB for the first 10TB per month
- Microsoft Azure: 100GB free, then $0.05-$0.18 per GB
- Google Cloud: Previously charged, but abolished egress fees for migrating to another provider in 2024
Even minor misconfigurations—like storing frequently accessed data across multiple regions—can silently drain budgets with high egress costs.
How to Reduce Data Egress Costs
- Optimize Cloud Architecture – Keep related workloads within the same region to avoid unnecessary cross-region transfer fees.
- Use Compression & Deduplication – Minimize bandwidth usage by compressing files before transfer.
- Implement Content Delivery Networks (CDNs) – Cache data closer to users to reduce retrieval costs.
- Buy Private Network Connections – Direct connections like AWS Direct Connect or Azure ExpressRoute often have flat-rate pricing for unlimited transfers.
- Monitor Usage Regularly – Set up spending alerts to track unexpected spikes in egress costs.
Data Egress Security Threats
Beyond financial costs, data egress is a major cybersecurity concern. Bad actors exploit outbound data flows to steal, leak, or manipulate sensitive information.
1. Malware & Ransomware Attacks
Malware enters a system through ingress data, often hidden in email attachments or infected software. Once inside, it exfiltrates valuable data via egress channels, sometimes encrypting it and demanding ransom payments.
2. Social Engineering & Phishing
Hackers don’t always rely on technical exploits. Phishing emails trick employees into sharing credentials or unknowingly transferring data to unauthorized recipients.
3. Insider Threats
Not all threats come from outside. Employees, either maliciously or accidentally, can exfiltrate sensitive data by sending files to personal email accounts, downloading documents onto USB drives, or uploading proprietary information to unauthorized cloud apps.
4. Unsecured Data Transfers
Unencrypted data in transit is vulnerable to interception. If an organization fails to implement TLS encryption or VPNs, attackers can snoop on outbound data flows and steal valuable information.
5. Excessive Permissions
If employees have more access than they need, it increases the likelihood of accidental or intentional data egress. A least-privilege approach limits unnecessary data exposure.
Best Practices for Securing Data Egress
1. Create a Data Egress Policy
Define clear guidelines on:
- Who can transfer data
- Where data can be sent
- What types of data require special handling or encryption
2. Deploy Firewalls & Configure Egress Filtering
A strong firewall strategy isn’t just about blocking inbound attacks—it should also monitor and restrict outbound traffic. Configure egress filtering to prevent unauthorized data transfers.
3. Implement Data Loss Prevention (DLP) Tools
DLP solutions use automated rules to:
- Detect and block sensitive data transfers
- Encrypt outbound files before transmission
- Prevent unauthorized file-sharing attempts
4. Monitor Network Traffic with SIEM
Security Information and Event Management (SIEM) tools provide real-time visibility into data flows, flagging suspicious activity before a breach occurs.
5. Encrypt Data in Transit & At Rest
Use TLS/SSL encryption for outgoing network connections. Sensitive files should be encrypted before transfer, ensuring stolen data remains unusable.
6. Control User Access
Implement role-based access control (RBAC) to ensure only authorized personnel can move high-value data.
7. Develop an Incident Response Plan
No security system is perfect. A well-defined response plan ensures that if a breach happens, the organization can act swiftly to contain damage and prevent future incidents.
Final Thoughts
Data egress isn’t just an IT concern—it’s a business risk. Unchecked egress can lead to security breaches, compliance violations, and massive cloud bills.
By implementing strong security measures, optimizing cloud architecture, and actively monitoring outbound traffic, organizations can protect their data and control costs.